A hacker group calling itself Scattered Lapsus$ Hunters has published a dark-web “data leak” website claiming to have stolen nearly one billion records from the Salesforce environments of dozens of organizations. The site lists approximately 39 victim companies, including major names such as Cisco, McDonald’s, KLM, Disney, Home Depot, and Adidas, among others. The threat actors are demanding ransom payments by October 10; if the deadlines pass without payment, they say they will publish the stolen data.
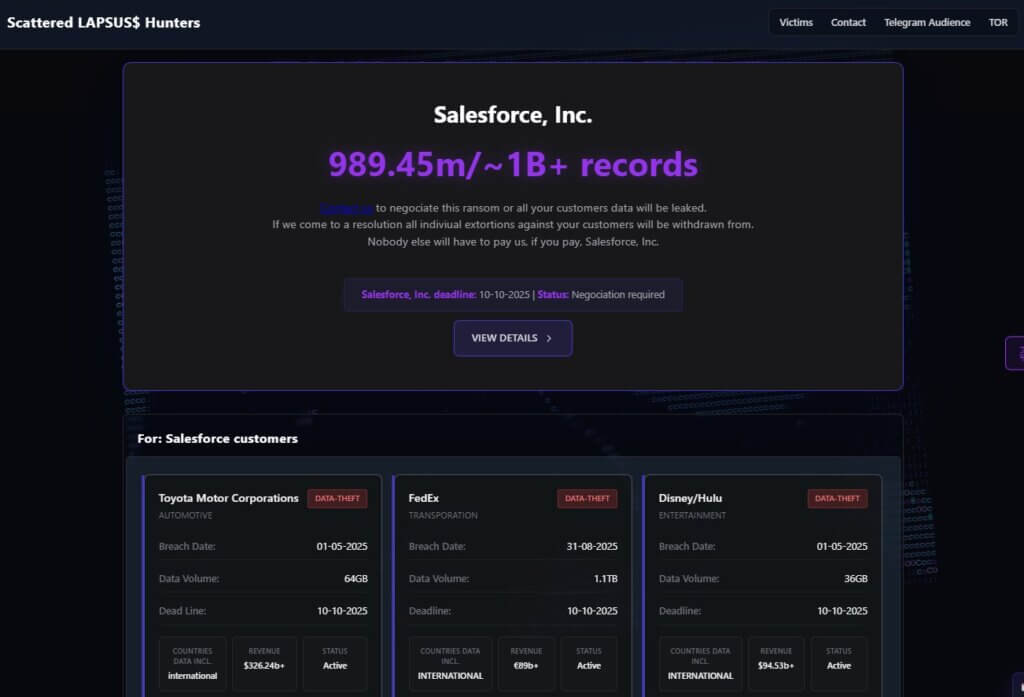
According to the extortion site, the stolen records include contact details, support-case information, transaction records, and personally identifiable data such as names, dates of birth, and passport numbers. Some security researchers tested samples of the data published on the site and found them to appear real.
Salesforce response: “no platform compromise” and no negotiation
In recent communications to customers, Salesforce has asserted that there is no indication the Salesforce platform itself was breached and that the extortion claims appear to derive from attacks on third-party integrations or customer environments. Salesforce also emphasized that these extortion attempts relate to past or unsubstantiated events, not new vulnerabilities in Salesforce’s own systems.
A Salesforce spokesperson confirmed the company will not negotiate, engage, or pay any ransom to the attackers. The company says it is working with affected customers and external experts, as well as law enforcement, to investigate and respond.
How attackers are said to have gained access
Security analysts believe the breach was carried out by exploiting a third-party integration between Salesforce and the Salesloft Drift application. Specifically, the attackers acquired OAuth and refresh tokens tied to the Drift application, which gave them access to Salesforce environments belonging to customers. Once inside, they exported data via standard Salesforce APIs and query tools.
Reports suggest that the threat actors used social engineering techniques, including “vishing” (voice phishing), to trick employees into granting access or installing a malicious version of Salesforce’s Data Loader. In some cases, employees were induced to connect unauthorized apps to their Salesforce accounts.
Google’s Threat Intelligence Group (GTIG) and Mandiant have published analyses showing that attackers systematically revoked and rotated Drift tokens, disabled the app, and issued security guidance. The compromise is not limited to the Drift application; in later phases, attackers also targeted email integrations tied to Salesloft.
Impact and uncertainties remain
While the extortion website lists dozens of companies, it is not yet confirmed whether every organization named was actually breached. Some firms have confirmed exposure of customer or employee data, while others are still assessing their incident response.
Because Salesforce insists its core platform was not compromised, the responsibility for security of integrations and connected apps falls to customers. The scale of the alleged theft—nearly one billion records—is difficult to independently verify.
What this means for customers
Salesforce customers should assume the possibility of compromise, especially if they used the Salesloft Drift integration. Many are urged to revoke and rotate all OAuth tokens and API keys, audit connected apps, review logs for suspicious activity, and investigate whether secrets (e.g., AWS keys, credentials) were compromised. Salesforce and Google’s threat teams have published detailed mitigation guidance for these steps.
Organizations should also coordinate with legal, compliance, and law enforcement teams, monitor for data leaks, and prepare disclosure and public relations strategies as needed. Given the extortion threat, companies may need to decide whether to make public statements or delay them until more facts are known.







