Red Hat has confirmed that a GitLab instance used by its Red Hat Consulting division was compromised by an unauthorized party.
The company says it “recently detected unauthorized access … removed the unauthorized party’s access, isolated the instance, and contacted the appropriate authorities.”
According to Red Hat, the affected GitLab instance is used specifically for consultant collaboration on certain engagements, not for its core product development or supply chain operations.
Red Hat further states that, to date, it has found no evidence that sensitive personal data was exposed.
Extent of alleged data theft and customer impact
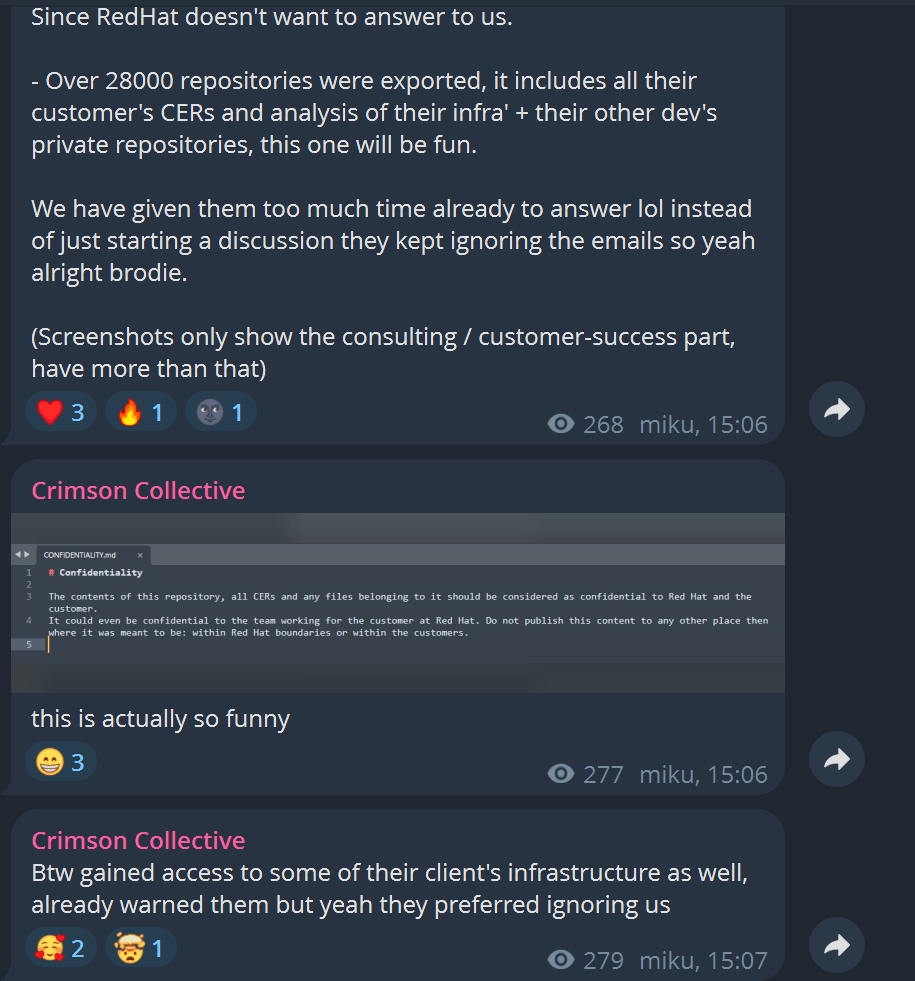
While Red Hat limits its confirmed scope, the threat actor group Crimson Collective claims a much larger haul:
- Approximately 570 GB of compressed data from more than 28,000 internal repositories.
- Within that, the attackers assert they obtained a number of Customer Engagement Reports (CERs) — internal consulting documents — numbering in the hundreds.
- The group claims that the stolen CERs include sensitive information such as network architecture, configuration details, authentication tokens, database URIs, and other credentials.
- They also allege that some of this data has already been used to access downstream customer infrastructure.
As proof, Crimson Collective has published directory listings, sample files, and screenshots to support its claims.
From these claims, the number of impacted enterprise organizations is estimated in the thousands (some reports suggest over 5,000), though Red Hat has not confirmed that figure directly.
Among the named organizations in leaked sample CERs or directory listings are high-profile firms across sectors — for example, banks, telecoms, airlines, and government bodies (HSBC, Walmart, ING, etc.).
Response and risk mitigation steps
Red Hat states that it is engaging directly with affected consulting customers and has implemented “additional hardening measures” to contain the breach.
Red Hat also emphasizes that it currently does not believe the breach impacts its other products, its software supply chain, or official download systems.
However, national cybersecurity authorities have issued warnings. For instance, Belgium’s Centre for Cybersecurity (CCB) assesses this incident as high risk for organizations that used Red Hat Consulting or shared credentials/tokens, and recommends immediate rotation of keys and tokens.
If your organization used Red Hat Consulting services, prudent steps include:
- Assume exposure of any credentials, tokens, keys, or configuration artifacts shared in projects with Red Hat.
- Rotate and revoke all credentials (API keys, database credentials, service accounts, certificates) that were used in or derived from Red Hat consulting engagements.
- Audit system logs for anomalous access—especially around the timeframe of the breach (mid-September 2025 onward).
- Review internal configurations referenced in engagement reports (network diagrams, VPN configs, scripts) for surprises or embedded secrets.
- Implement enhanced monitoring and alerting for lateral movement, authentication anomalies, or access from new endpoints.
- Engage Red Hat support and request copies of the stolen files (or a disclosure of what portion of your data was affected).
Uncertainties and open questions
- Red Hat has not validated all the claims made by Crimson Collective, particularly regarding exactly which customer data repositories were exfiltrated.
- The method of initial access and root cause remain undisclosed.
- It is unclear how many customers (or what proportion of those named in the directories) had substantial exposure.
- The timeline of when the intrusion occurred versus when it was detected is still under investigation.
- Final confirmation of whether personal or sensitive data was exposed is pending further forensic analysis.
Outlook and implications
This breach highlights a key risk vector: consulting and third-party access environments. Even if core software and supply chains are insulated, consulting platforms that touch client systems can become high-value attack surfaces.
If the claims hold, the downstream risk is significant: adversaries equipped with internal architecture information and credentials may more easily penetrate customer systems, launch targeted attacks, or pivot laterally.
Organizations who have used Red Hat Consulting should treat this incident as a possible initial reconnaissance advantage for attackers, and respond as though sensitive design documents or credentials might already be weaponized.







