In a major security disclosure on October 8, 2025, SonicWall confirmed that threat actors have stolen firewall configuration backup files for all customers who used its cloud backup service. Previously, the company had stated that fewer than 5 percent of customers were impacted via brute-force attacks. The updated finding supersedes that earlier scope assessment.
SonicWall’s investigation, conducted in coordination with Mandiant, concluded that an unauthorized party accessed the MySonicWall cloud backup storage and retrieved firewall “preference files” for every customer that had ever used the cloud backup feature. These EXP files include the full snapshot of a firewall’s configuration at the time of backup—including settings, rules, and encrypted credentials. While credentials and secret keys inside the files remain encrypted (in newer “Gen 7 and newer” devices, they are individually encrypted using AES-256), other portions of the configuration are encoded or readable. Possession of the full file gives threat actors a structural blueprint of networks, which could facilitate more targeted attacks.
Initially, SonicWall had described the incident as brute-force attacks targeting less than 5 percent of customers. Those references have since been removed from the official disclosure, and the updated advisory does not mention brute forcing as the cause of the breach.
Risks to affected customers
Even though credentials in the files were encrypted, the configuration data can provide attackers with knowledge about network topology, VPN settings, SSL/TLS and certificate uses, IP addressing, firewall rules, and other metadata. With that information, attackers may be better positioned to launch targeted attacks—such as credential guessing, lateral movement, or exploiting devices or services exposed by the configuration.
Because all cloud-backed configurations were exposed, any organization that used the backup feature must assume potential compromise of their stored backups.
SonicWall’s response & guidance
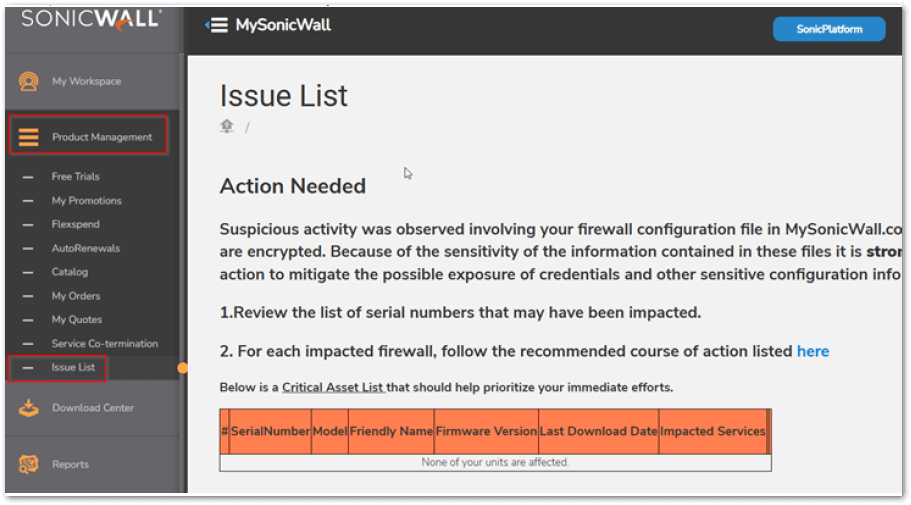
In its public advisory, SonicWall says it is notifying all affected partners and customers and has published tools to help assess and remediate impacted devices. In the MySonicWall portal, an “Issue List” page under Product Management now flags device serial numbers and classifies them as “Active – High Priority,” “Active – Lower Priority,” or “Inactive.” These labels help users prioritize which devices to remediate first.
SonicWall also says that it has implemented unspecified “additional security hardening measures” and is working with Mandiant to improve its cloud infrastructure and monitoring systems.
Customers are urged to log into MySonicWall and check if their devices have cloud backups. If so, they should check whether their serial numbers appear on the Issue List. If a device is flagged, it should follow the containment and remediation playbook provided by SonicWall. Some of the immediate recommendations include resetting all credentials, reviewing enabled services, disabling remote management access over WAN, and importing a new configuration that removes compromised secrets.
As of October 8, SonicWall says its investigation is complete, and the disclosure is now final.
What remains unknown
SonicWall has not disclosed how the attackers gained access to the cloud-stored backups at scale. The company’s updated statement omits the earlier reference to brute-force attacks. It is not clear whether vulnerabilities, credential compromise, or internal misconfigurations played a role.
Another unanswered detail is whether the stolen files have been leaked publicly or used maliciously already. SonicWall does not currently claim any public exposure beyond the breach itself.
Also unknown is precisely what the “additional security hardening measures” are, or how customers should validate that their environments are fully secure going forward beyond following remediation guidance.
Implications & next steps
This incident underscores the risk inherent in centralized cloud backups of sensitive system configurations. The assumption of encryption alone is insufficient when an attacker gains wholesale access to stored files.
For organizations using the MySonicWall cloud backup service, the imperative is clear: verify if you were impacted, contain compromised devices, rotate all credentials and keys, and assume that adversaries have a detailed map of your firewall settings.
Longer term, this may prompt enterprises to reevaluate reliance on cloud-based storage of configuration snapshots or to demand improved security controls (such as zero-trust, limited access, multi-party encryption) from vendors offering such features.